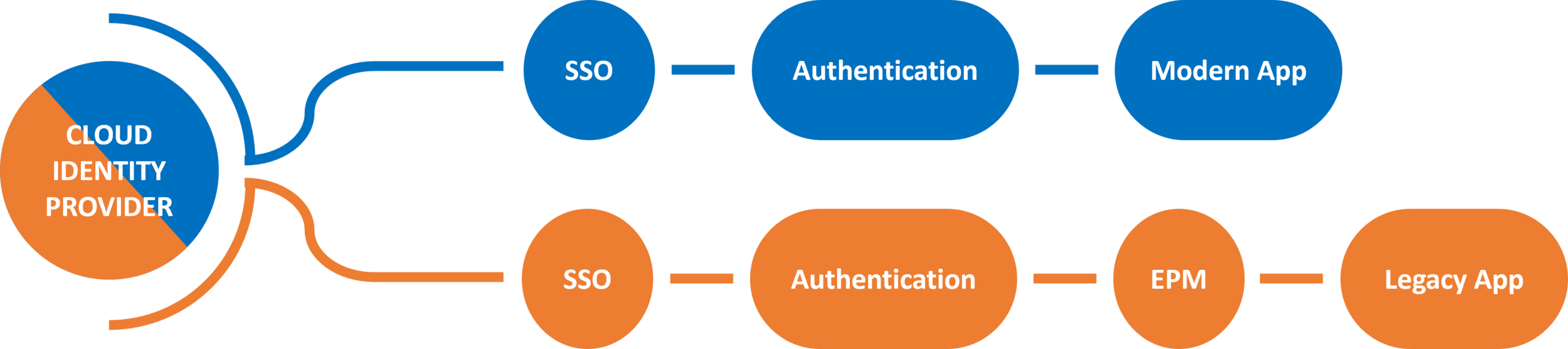
Match Enterprise Password Management and Cloud SSO for simple & secure access
Where EPM’s stand in current day enterprises
Everyone loves Single Sign On. It’s a simple way to securely provide your staff with accesses to their application & service. By tying access to a single, well secured identity, an organization can reduce it’s attack surface & cybersecurity risk. Ultimately, staff can get to their work done faster and more securely.
However, SSO capability usually isn’t available for all applications. For example, legacy applications rarely support SSO technologies like OpenID and SAML. In other cases, the SSO capability is hidden behind a hefty pay wall, such as with the Adobe Creative Suite for Enterprise.
When faced with a situation where SSO is unavailable, an EPM is one of the best next options. A strong EPM solution simplifies identity management by securely generating, storing and providing logon information.
What does an Enterprise Password Management solution provide?
1. It allows to extend the SSO experience to non SSO applications
By putting your EPM behind your SSO solution, you allow your staff to achieve 2-click logon to your non SSO apps, without compromising on security
2. It gives a secure way to enable shared credentials
A powerful EPM solutions uses internal secured channels for shared credentials. You no longer need employees to send cleartext password over text messages or emails
3. It improves your cybersecurity stance through transparent policies
You can establish password policies directly within the EPM to ensure that generate passwords have a high-level of complexity, thus a high resistance against password sprays and brute force accounts. Every password is unique, while the complexity is abstracted from staff so they can focus on accessing their systems.
4. Helps reduce the load on your helpdesk
Using the SSO towards your EPM, staff have access to all their enterprise credentials, which they can update, share and delete as they see fit. The EPM solutions takes care of remembering the passwords, so your staff no longer have to rely on helpdesk for constant resets.
Integrating an EPM into a cloud native or hybrid organization to extend cloud identity?
1. Make sure your identity provider service is up to level
When integrating your EPM in your cloud identity strategy, your Cloud Identity Provider serves as the front door to the EPM system. Thus, it is important to ensure that
1. You ISP has SSO capabilities
2. You have a validated cloud identity security strategy
This strategy can include MFA, conditional access, and more. In our case, we’ll be using Azure AD, our CIP of choice for anyone using Microsoft 365 and/or Azure.
Please note that the extend at which you can implement different features often depends on your cloud identity provider’s licensing.
Some other compatible solution includes GOOGLE, OKTA and JUMPCLOUD
2. Choose an EPM solution
Choosing an EPM that works with your enterprise is crucial, as it will dictate a large part of the user experience. Relevant choices include LastPass, Bit warden, Nord Pass and DashLane and many more.
We often recommend Bitwarden. It strikes a good balance between feature set, useability, and cost. Furthermore, Bitwarden is open-sourced. This adds transparency and trust, which is an essential aspect to the applicability of a EPM within an enterprise context.
3. Choose between a cloud-hosted or self-hosted mode
Depending on your EPM of choice, you may have the option to self-host the system. Self-hosting is interesting for enterprise with complex security, private and data integrity obligations.
At Marlon Group, we’ve found that using the self-hosted version of an EPM hosted within a self-owned cloud environment creates the perfect balance between practicality, availability, security and privacy. However, expect to pay a slight premium to host these solutions. They are most often not intensive resource wise, and you may be able to get away with free tier hosting resources (but we didn’t tell you that).
4. Link your IP with your EPM through SSO
Each EPM & IS supports different technologies enabling SSO, but the two most common are OpenID Connect and SAML 2.0. In our case, we’ll be using SAML 2.0.
1. Inside of Azure AD, create an Enterprise Application for your EPM.
2. Activate the SSO feature inside of your EPM Solution.
3. In your Enterprise Application, head to the Single Sign-On blade and copy the relevant settings from your EPM solutions.
4. Likewise, you’ll need to copy a few settings from Azure AD onto the EPM
5. After copy pasting the pertinent information, your SSO should now be active. You may want to enable policies such as SSO Authentication, Single Organization & Master Password Reset to make your implementation uniform & manageable. Unsolicited SSO assertions can be enabled to simplify user experience a touch further.
5. Train your users to use the EPM
Your EPM Provider should have a readily available stock of training content for your staff base. It’s important to make sure they have access to this info and make sure that they invest the time to watch over it. Communicate with your staff that the EPM solution is here to make their life easier!
Still don’t know where to start with your password management journey? Go to our contact us page for a free consult.